The 2020 identity highlights as noted by IDnextplatform. Digital identity is well and truly established as one of the most significant technology trends on this planet. Like every year, IDnextplatform is keeping a close eye on several identity resolution trends that will usher in a new digital era.
We can conclude that new technologies and regulations are supporting the digital transformation ahead. Therefore, we have highlighted several of them. This should help you explore the trends in the world of digital and provide the insight and inspiration you need.
Robert Garskamp – Founder IDnextplatform
2020 – The year of “good” Digital Identity?
Introduction
The year 2019 brought plenty of developments impacting the digital world. Digital espionage and manipulation of information. Data breaches on a yet larger scale, increased awareness of the rights to data protection in the aftermath of the launch of GDPR. Cybercrime was growing ever faster in volume and diversity, and the Internet of Things was enabling more and more automation.
All of this was happening against a backdrop of Brexit, imminent trade wars, surging civil protests against governments, and climate change. What to expect in the digital 2020? Will 2020 be the year of “good digital identity”? And what are the main trends in the digital identity domain?
Setting the scene for digital identity
“For years, we have been discussing, implementing and improving trustworthy and interoperable digital identities. And we have already come a long a way: what started as a wide range of different, fragmented, insecure and inconvenient point-point solutions has evolved through the years to a number of large-scale ecosystems with trustworthy, user-friendly, privacy-enhancing eIDs that can be used cross-border and cross-domain, cross-service,” says Eefje van der Harst, project manager at The Data Sharing Coalition. 
But their coverage is still scattered. And interoperability of digital identity schemes is still a nightmare. Even after decades, ineffective identity siloes, and complex jungles of identity federations are still defining the landscape. Biometrics technology has improved the usability of login mechanisms for end users. But complexity, lack of transparency, and over-sharing of personal information in a scattered identity landscape are still the rule when it comes to authorisation management and digital enrolment.
The problem of trustworthy remote identification for online enrolment has still not been solved satisfactorily. At the same time, more diverse transaction types are conducted online, and the trust level of digital identities needs to be ever higher because more high-risk processes are run digitally.
Also, physical processes are becoming increasingly dependent on digital processes (e.g., automation of supply chains, smart cities). Location-independent online services, delivered via platforms, connected via APIs, and using complex global delivery chains all require even more interoperability and portability of trust.
In all digital transformations, digital identity remains the persistent factor, acting as a security perimeter for individuals, things, devices, and organisations.
In short: digital identity is becoming crucial for almost all aspects of physical and digital life and is becoming extremely complex rather than easier and more secure.
Eefje: “What is still lacking in e-ID ecosystems are generic, standardised and interoperable authorisation mechanisms. A common language or a set of protocols and interfaces that makes it easier, yet secure, for service providers to establish that what you can do in their service because they know it is you, or because they can trust someone/thing (machines, things and people) is mandated or delegated and thus acting on your behalf. Will 2020 be the year in which we focus on what according to most experts is the final missing piece in the eID ecosystem puzzle: Access?” she wonders.
So, there is still no silver bullet to make things better. Or is there light at the end of the tunnel?
Identity in 2020
There is some good news indeed. Both on a national and an international level, there are numerous initiatives to improve the usability and interoperability of digital identity, and the EU-identity scheme e-IDAS for citizens is gaining coverage (9 EU member states have notified, 3 pre-notified, the Netherlands pre-notified in December 2019 with DigiD).
“Initiatives such as EIDAS, providing guidance and advocating interoperability are very helpful” according to Andre Koot, IAM security consultant at Nixu. Yet he states that two other IT security developments are helping as well. 
The first, Zero Trust Architecture (ZTA) is a principle that allows network communication only after explicit validation of trust. Cryptography is used (among others) to establish this. A more technical explanation is given in the figure below.
The second is the development of API gateway technology, enabling network communications via modern protocols. Combining these developments with Access Policy Management can create a fine-grained fabric of access controls. Policy-based access control and zero trust architectures are a basis for the new access control methods.
According to the draft Nist SP800-207 guidelines, Zero Trust is the term for an evolving set of network security paradigms. Instead of focusing on defences for wide network perimeters they focus on individual or small groups of resources. This definition is a clear interpretation from the old “Jericho” security paradigm: using fine-grained access control to data elements: “never trust, always verify”. Zero Trust Architecture cannot be seen as networking security controls only (segmentation, encryption of all communication between components). The concept of (access) ‘policy-based access control’ (as an evolution of attribute-based access control) is an important element in governing access, as can be seen in this Nist figure below.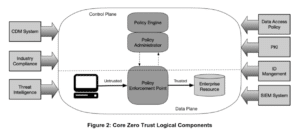
Some European member states are already using privacy-friendly mobile identity solutions with large-scale coverage across the private and public sector and multiple industries. The coverage of the Belgian mobile ID ITSME is a good example.
Eefje: “We have seen some promising initiatives being developed in the identity area (e.g., eHerkenning, iSHARE) each working in their own domain (Business-to-Government, Business-to-Business). But in 2020, I am hoping to see more generic authorisation solutions that work cross-border, cross-domain, cross-sector and cross-service. Because in the end: enabling access is what e-IDs should be all about!”
 Jacoba Sieders, independent identity strategist: “Even the World Economic Forum, in its publication on digital identity in January 2020, addresses the topic. It emphasises the importance of good digital identity as a crucial and strategic element for good and fair digital life for all. It stresses the principles of data protection, usability, and data minimisation, as well as the other requirements for a good digital identity. Multinational companies in various industries have already embraced these principles. These are signs that good digital identity is no longer the restricted domain of technical discussions, but that it is on the agenda of decision makers and business leaders as a key factor for digital citizen’s rights. To me, this gives some hope for the future.”
Jacoba Sieders, independent identity strategist: “Even the World Economic Forum, in its publication on digital identity in January 2020, addresses the topic. It emphasises the importance of good digital identity as a crucial and strategic element for good and fair digital life for all. It stresses the principles of data protection, usability, and data minimisation, as well as the other requirements for a good digital identity. Multinational companies in various industries have already embraced these principles. These are signs that good digital identity is no longer the restricted domain of technical discussions, but that it is on the agenda of decision makers and business leaders as a key factor for digital citizen’s rights. To me, this gives some hope for the future.”
Self-Sovereign and multi-sourced Identity
Apart from these emerging good initiatives for good digital identity, 2020 will bring more Self Sovereign Identity (SSI) ecosystems. The concept was developed some years ago. Today, it is known as the next big thing for the secure and privacy-preserving sharing of data across trusted parties – both individuals and organisations. Standardisation of the identifiers has been largely developed. Standardisation on Blockchain identities is even addressed by standardisation organisations, since Blockchain is often seen as a good technology to support SSI.
The European Union is developing its Europe-wide version called ESSIF, EU member states and, for instance, the government of Catalunya are developing their own, and the technology is being perfected. e-IDAS-supported Self-Sovereign Identity is under investigation as an option. In the Netherlands, the private and public sectors are finding each other in working groups to try for a Dutch passport-grade public and private digital passport. Interesting in this respect is the launch, in January 2020, of the Dutch Legislation for the Digital Government, setting the boundaries and criteria for citizens’ and companies’ interaction with the government.
Jacoba: “Self-Sovereign Identity will be the preferred model, but it will take a long time to establish predominant coverage. The technology is available, some POCs have evolved towards functioning solutions in production. But a major problem remains how to address governance and liability matters for the complex ecosystem of roles and responsibilities that SSI requires. Legal frameworks are not yet ready to handle this complexity, but partners contributing to an SSI ecosystem need legal security. My prediction is that a new discipline will emerge in the legal domain, finding the best legal set-up for (identity) services owned by a coalition of multiple independent legal entities, to address liabilities, accountabilities, and business aspects in a fair way. The same aspect is relevant for Blockchain-based shared solutions.”
Self-Sovereign Identity (SSI)
The generic idea of SSI is that users are self-sovereign, in control of their personal information.
The user owns some type of secure (mobile) wallet containing identity proofs and claims (date of birth, driver’s licence, education degree) The portable identity claims are reused with numerous relying parties for authentication or enrolment. Multiple authoritative sources (“issuers”) together contribute their data to build the identity (“multi-sourced identity”). It is the user who decides what is shared. Issuers and relying parties who want to trust those claims (“verifiers”) have to agree on trust levels and on participating in the ecosystem. Common agreement about the claims and their semantics is important. In many cases, distributed ledger technologies are used for SSI e.g., to keep the transactions of the user untraceable, and to facilitate the exchange of Zero Knowledge Proof.
Creating large-scale self-sovereign identity ecosystems is a difficult and tedious task requiring complex cooperation.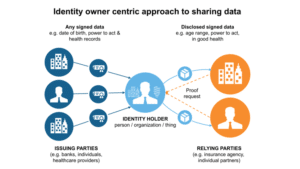
Digital enrolment
Now that biometrics and Multi Factor Authentication technologies have matured and gained broad adoption, authentication risks may become smaller. Yet the first step, the creation of a trustworthy digital identity during the enrolment phase, still poses a significant risk when this is done online. The past two years saw a wave of start-ups addressing this topic. Legislation is not very precise in prescribing the technical boundaries for digital enrolment requirements and varies across geographies. For industries where identification-related operations are regulated, there is no clear silver bullet to solve this. In banking, shared services for customer identification, verification, and background checking are emerging to reduce their immense costs and to avoid risk related to digital enrolment and identity theft. Formal acceptance of multi-sourced identity solutions might help. European passports contain chips with identity data of the holder, which can be read by chip-readers in mobile phones. Accessing this chip-data is regulated, and not all data can be read. In 2020, Brexit requires all British citizens to identify themselves personally at their local administrations. A remote identity verification solution to support this process online is being adopted. This would be the first large-scale use case with millions of identities to be verified online.
Privacy
According to Arnold Roosendaal, Director of Privacy Company,  the privacy landscape will continue to evolve in 2020. Most organisations have made progress on becoming GDPR compliant. The paperwork has been done, so the next step to focus on will be privacy management in order to maintain compliance and demonstrate being in control. Specific activities that will increase are the performance of Data Protection Impact Assessments (DPIA) and allocating tasks for privacy officers and data protection officers (DPO). E-privacy remains on the agenda, and big steps depend on the decision-making process for the new Regulation.
the privacy landscape will continue to evolve in 2020. Most organisations have made progress on becoming GDPR compliant. The paperwork has been done, so the next step to focus on will be privacy management in order to maintain compliance and demonstrate being in control. Specific activities that will increase are the performance of Data Protection Impact Assessments (DPIA) and allocating tasks for privacy officers and data protection officers (DPO). E-privacy remains on the agenda, and big steps depend on the decision-making process for the new Regulation.
Peter Hoogendoorn, managing consultant at Cap Gemini,  expects that, triggered by GDPR and some high-impact breaches, companies will start to explore data-minimisation to reduce cost and processing burden at the same time.
expects that, triggered by GDPR and some high-impact breaches, companies will start to explore data-minimisation to reduce cost and processing burden at the same time.
According to Inge de Ruijter, Associate Director, Bridgehead,  consumer awareness is growing and now that GDPR is in place, data protection could be seen as an element of sustainability and good behaviour for companies.
consumer awareness is growing and now that GDPR is in place, data protection could be seen as an element of sustainability and good behaviour for companies.
A very different and positive side effect of the launch of GDPR is that users today, next to privacy-aware, are also more cybersecurity-aware. Statistics of phishing incidents have fallen, although the latter is probably partly due to improved authentication technology.
But the Internet of Things will bring more and more difficult challenges.
Peter: “Ransomware and state-driven espionage will manifest themselves in a few large breaches that will force institutions and companies to rethink their security strategy. Especially vulnerable Internet of-Things (IoT) systems will show a few large breaches. Security solutions in the IoT environment will become more mature and embedded in the design.”
Blockchain
The concept of digital cash based on the distributed ledger technology as published by Satoshi Nakamoto in his whitepaper saw its 10th anniversary in October 2018. For most people, digital currencies are the main block chain applications they know. Today in 2020 there is a wide variety of distributed ledger types, derived technical solutions, and use cases. Block chain has grown beyond its infancy of POCs-only with no follow-up. The classical question here is: “Why use block chain?” In most use cases, a regular database solution satisfies the needs. But wherever crucial documents need to be shared across widely diverse parties who cannot be governed by a single authority, whose systems are not connected, and where trust in data integrity and availability are key, there may be a good business case to use distributed ledger technology. Self-Sovereign Identity ecosystems and Global supply chain use cases are the most prominent examples in place today. They require dynamic constellations of a wide range of partners in a transaction, who need to share one administrative process. Peter: “This year will see the change from proof of concept to real, live production systems. Self-Sovereign Identity frameworks will start to pave the way to customer adoption of Blockchain-based Identity Management.”
Conclusion
Establishing a “good” digital identity ecosystem is a difficult problem, which has still not been solved in 2020. And “good” in this context means portable, robust, dynamic, high-trust, frictionless, completely interoperable, privacy preserving, and secure. Technology is not the prime barrier. Governance, standardisation of technology in use, fragmentation and lack of cooperation across industries and public and private sectors are.
But there are good signs and there is hope. On a national and international level, Self-Sovereign Identity (SSI) ecosystems are high on the agenda, giving the users control over their own personal data. SSI will become mature, and it will also be adopted by public organisations. SSI will be pushing organisations of completely different domains to work together in working groups and coalitions, something that is already happening today. In 2020, existing and emerging examples of “good” digital identity ecosystems will gain support and pick up larger coverage, supported by the trends of security- and privacy-awareness. Zero Trust Architectures are emerging to ensure more security.
Legal frameworks, however, still need to be adjusted and designed to support dynamic cross-sector trust models. This is an important precondition for many organisations to feel comfortable in taking part in multi-party identity ecosystems, where liabilities need to have a clear legal anchor. It will take much time and effort to address this.
Leaders in business and in government are beginning to see the importance of good digital identity. This will leverage the current trends of SSI and the expansion and adoption of “good” identity.
The identity of things, however, will bring more and more new challenges. Data breaches and security incidents will be more disruptive in 2020 and have a growing impact on our physical day-to-day life.
But, yes! 2020 will be bringing us many steps forward towards “good” digital identity, and we are looking forward to exciting developments into the right direction!
Resources for further reading
World Economic Forum on digital identity: http://www3.weforum.org/docs/WEF_Digital_Identity_Strategic_Imperative.pdf
EU eIDAS and SSI:
https://ec.europa.eu/futurium/en/system/files/ged/eidas_supported_ssi_may_2019_0.pdf
eIDAS community page EU: https://ec.europa.eu/cefdigital/wiki/display/EIDCOMMUNITY/Overview+of+pre-notified+and+notified+eID+schemes+under+eIDAS
Dutch Digital Government legislation (‘Wet op Digitale Overheid NL’): https://www.eerstekamer.nl/wetsvoorstel/34972_wet_digitale_overheid (Dutch only)
ESSIF: https://medium.com/@HodlHelper/essif-the-european-self-sovereign-identity-framework-4572f6875e12
EU Blockchain ID: https://www.eublockchainforum.eu/news/being-ourselves-everywhere-blockchain-and-european-e-identity-framework
eIDAS and ESSIF opinions: https://ec.europa.eu/futurium/en/eidas-observatory/ssi-and-eidas-vision-how-they-are-connected-share-your-views
McAfee: https://www.mcafee.com/blogs/other-blogs/mcafee-labs/mcafee-labs-2020-threats-predictions-report/
Verizon Data Breach Investigation Report 2019: https://enterprise.verizon.com/en-nl/resources/reports/dbir/
Catalan SSI: https://www.ledgerinsights.com/catalan-government-self-sovereign-identity/



