Every year, the IDnextplatform’s Advisory Board presents a summarized report that gives an overview of the latest developments within the world of Digital Identity. The Advisory Board plays a vital role for the IDnextplatform and consists of distinguished experts from around the world. They are committed to keeping IDnext on the cutting-edge of digital identity practices and ensuring that IDnext is the premier platform of state-of-the-art services to its members.
The Advisory Board also provides independent advice to the Executive Board regarding the direction and activities of the IDnext association.
Why are we doing this? Millions of people around the world are ‘invisible’, but technology will play an increasingly important role in society and give these people an identity. O en, this involves positive developments that make life easier and more pleasant, but at the same time, render it less secure – and don’t we unwittingly cross ethical boundaries that we’d have preferred to avoid if we’d understood the consequences of those developments better?
It also involves using digital technologies that remake a process to become more e cient or e ective. The idea is to use technology not just to replicate an existing service in a digital form, but also to transform that service into something signi cantly better.
This becomes more and more important in a progressively digital world. All technological developments have their pros and cons. In this period of contemplation, it is recommended that we think about what those developments mean for us and how we can deal with them in a mature way.
Let us give you an overview of a number of developments that we foresee in 2022. On this page we also share an overview of topics from previous trend reports.
R.L. Garskamp – Founder IDnext platform
IDnext trends 2021 and 2022
Covid-19 accelerated the roll-out of digital identity services. Many of these services had already been available, but the sudden reality of working from home triggered the faster implementation of online authentication and authorization for employers.
On the consumer side, more groceries were ordered online during this period. Even though restaurants were closed, they also saw a lot more business, due to take away/delivery of food. Consumers are looking for a touchless experience by using technology solutions such as face identification, and connected accounts facilitate ordering, payment, and verification of address details.
As many educational institutions were closed, remote learning has become very important for students. Though various remote learning solutions had existed before, their adoption increased during this pandemic. There are more online one-to-one classes in areas such as music, art, yoga etcetera.
Partly due to data breaches of public health databases, another effect of Covid-19 is that the awareness concerning the necessity of proper security and privacy measures increased.

This trend report gives an overview of the trends on identity and privacy in 2021. Previously existing trends are described along the lines of their Covid-19 impact. New trends are divided into policy, business, and innovation. Lastly, some predictions for 2022 are given.
- “2022 will be the starting point of a stronger legal position and demand of the consumer in deriving value from data when purchasing goods or digital content. Consequently, a step up is required in the infrastructure supporting merchants and individuals in respectfully identifying themselves, sharing personal data with privacy and consent in return for goods and services.”
Inge de Ruijter (Advisory board IDnext)
- “The password-less society will reach a major breakthrough in 2022.”
Peter Hoogendoorn (Advisory Board IDnext)
- “Know Your Employees is becoming the KYC version for your workplace.”
Martin Sandren (Advisory Board IDnext)
Looking forward
As 2021 has brought a lot of developments, but also pointed out weaknesses and challenges, the question is what the upcoming years will bring:
- “Increased adoption of decentralized Identi- fiers, trust frameworks”
Bharadwaj Pulugundla (Advisory Board IDnext)
- “Increased privacy awareness will make citizens/consumers more demanding with regard to privacy and security measures. Organisations will really have to demonstrate their privacy maturity to be trusted.”
Arnold Roosendaal (Advisory Board IDnext)
- “Digital identification will be legally guaran- teed in 2022.”
Poppe Wijnsma (Advisory Board IDnext)
To conclude
Covid-19 has accelerated many of the developments in privacy and identity. In 2022, this trend will continue. Organizations are more aware than ever of the impor- tance of proper identity management in combination with privacy and security. This will help individuals in gaining more control over their personal data.
Interested in ALL trends of 2022 and 2021? Please send us an e-mail to request the whole document.
__________________________________________________________________________________________________________________________________________________________________________________
Overview of previously published trend reports:
Identity in 2020
Both on a national and an international level, there are numerous initiatives to improve the usability and interoperability of digital identity, and the EU-identity scheme e-IDAS for citizens is gaining coverage (9 EU member states have notified, 3 pre-notified, the Netherlands pre-notified in December 2019 with DigiD).
“Initiatives such as EIDAS, providing guidance and advocating interoperability are very helpful” according to Andre Koot, IAM security consultant at Nixu. Yet he states that two other IT security developments are helping as well.
The first, Zero Trust Architecture (ZTA) is a principle that allows network communication only after explicit validation of trust. Cryptography is used (among others) to establish this. A more technical explanation is given in the figure below.
The second is the development of API gateway technology, enabling network communications via modern protocols. Combining these developments with Access Policy Management can create a fine-grained fabric of access controls. Policy-based access control and zero trust architectures are a basis for the new access control methods.
Some European member states are already using privacy-friendly mobile identity solutions with large-scale coverage across the private and public sector and multiple industries. The coverage of the Belgian mobile ID ITSME is a good example.
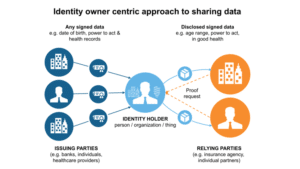
Self-Sovereign and multi-sourced Identity
Apart from these emerging good initiatives for good digital identity, 2020 will bring more Self Sovereign Identity (SSI) ecosystems.
The generic idea of SSI is that users are self-sovereign, in control of their personal information.
Privacy
According to Arnold Roosendaal, Director of Privacy Company, the privacy landscape will continue to evolve in 2020. Most organisations have made progress on becoming GDPR compliant. The paperwork has been done, so the next step to focus on will be privacy management in order to maintain compliance and demonstrate being in control.
Blockchain
Block chain has grown beyond its infancy of POCs-only with no follow-up. The classical question here is: “Why use block chain?” In most use cases, a regular database solution satisfies the needs. But wherever crucial documents need to be shared across widely diverse parties who cannot be governed by a single authority, whose systems are not connected, and where trust in data integrity and availability are key, there may be a good business case to use distributed ledger technology.
Interested in the other trends? please send us an e-mail for request of the whole document.
_____________________________________________________________________________________________________________
IDnext trends 2018
API – the interaction world

The trend of introducing federation technologies is moving forward even within back offices of organizations, thus enabling the adoption of fine-grained dynamic ABAC, using modern federation-style protocols such as SAMLv2, OAuth V2 and OpenID Connect. The traditional access control framework has been defined in the XACML standard. Implementing this standard is no small feat: it requires a lot of work finding and creating tools and customizing the implemented solution. In practice, we don’t see XACML implementations.
But a work-around is developing. In order to parse the information and be able to transfer and convert the access information, we can use one of the newer networking tools that have been introduced as a result of digitization and migration to the new low-code, DevOps and micro-service architectures. API security gateways will do the job. The transformation of business applications to a service and micro-service architecture will help us implement ABAC. This migration is enabled by federation-style protocols and requires new access mechanisms. And these mechanisms will be built around API Security Gateways.
To be able to separate normal API usage patterns from attack usage patterns, the use of AI engines is emerging.
Interested in ALL trends? Please send us an e-mail to request the whole document.
__________________________________________________________________________________________________________________________________________________________________________________
IDnext trends 2017
Technology will play an increasingly important role in society – these are often positive developments that make life easier and more pleasant, but also they render it less secure – and don’t we unwittingly cross ethical boundaries that we’d have preferred to avoid if we’d understand the consequences of those developments better?
These questions become more important in an increasingly digital world. All technological developments have their pros and cons. In this period of contemplation, it is recommended that we think about what these developments mean to us and how we can deal with them in a mature way.
Let us give you a number a developments that we foresee for 2017!
Attribute based control
Lastly, there is a trend or direction for IAM. Most corporate organisations have a working IAM solution, aimed at internal staff. The logical access control model companies work with is often based on Role Based Access Control (RBAC). This is a static model, which is in need of innovation, especially since the IT landscape has also changed drastically thanks to cloud applications and BYODs.
The sequel to this is the dynamic model, Attribute Based Access Control (ABAC). Last year, there was much talk of this, however, few organisations have as yet made headway with this development. Those organisations that currently make use of ABAC mostly deploy it from a technical point of view. The transition /migration of roles to rules /attributes and actually adding business value demand time and effort. This is what organisations will focus on.
This technology is also deployed as a safe and simple way of providing access to clients and partners. Often, the clients of an organisation cannot easily communicate between various domains.
Thus, a client of, for example, a bank may purchase services privately as well as corporately. For customers like that, many identities need to be managed, far more than for the internal staff, but also changing back and forth between these domains is a challenge. For the IT organisation and the business this brings along vast effort and a multitude of risks. The focus for the near future will be on offering standards for better/ simpler authentication for clients, providing access to business partners in a secure and easy way and implementing complexity reduction for both the business and the IT division.
Interested in the other trends? please send us an e-mail for request of the whole document.